Looks like the password phishers are finally starting to learn proper grammar and piece together something kinda convincing. Here’s a breakdown on one that I had reported to me over the UMD holiday break. It’s notable for a few reasons:
- Timing – it was sent over holiday break when lots of academics will be working, but normal administrative/IT staff is off.
- ‘Realness’ , from copies of UMD’s actual page to references to actual IT help email addresses and phone numbers it passes the sniff test.
- Attention to detail – Lots of the domain names, etc are put together in a way that won’t raise an alarm to most folks.
Step 1, The email
Here’s the actual email received from these guys. A few things they got correct:
- The signature information (sans Access & Delivery Services department) is all real and correct.
- The name of UMD’s IT helpdesk and the included email is correct.
- Most of the display part of the URL is correct and UMD does have a CAS sitting at /cas/login with the obvious switching of lib and edu.
Sent: Friday, January 1, 2016 9:29 AM
To: xxxxx@umd.edu
Subject: Library Services
Your access to your library account is expiring soon, and you will be not eligible for Document Delivery Service. To continue to have access to the library services, you must reactivate your account. For this purpose, click the web address below or copy and paste it into your web browser. A successful login will activate your account and you will be redirected to the library homepage.
https://umd.edu.lib/cas/login&service=httpsAFFshib.idm.umd.eduFshibboleth-idpFAuthnFRemoteUser&connect.FpublicFpreauthConnect&allow=umd.jsp/
Kind Regards,
University of Maryland Libraries
McKeldin Library, College Park, MD 20742
Phone: 301-405-0800
Step 2, the URL
* Hostname was NOT found in DNS cache
* Trying 185.28.21.95…
* Connected to univ-library.ga (185.28.21.95) port 80 (#0)
> GET /activation/access/link.php?M=11158&N=40&L=11&F=H HTTP/1.1
> User-Agent: curl/7.35.0
> Host: univ-library.ga
> Accept: */*
>
< HTTP/1.1 302 Moved Temporarily
< Date: Fri, 01 Jan 2016 21:00:50 GMT
* Server Apache is not blacklisted
< Server: Apache
< X-Powered-By: PHP/5.5.26
< Location: http://umd.edu-lib.ml/cas/login&service=httpsAFFshib.idm.umd.eduFshibboleth-idpFAuthnFRemoteUser&connect.FpublicFpreauthConnect&allow=umd.jsp/
< Content-Length: 0
< Content-Type: text/html
<
* Connection #0 to host univ-library.ga left intact
univ-library.ga has address 185.28.21.95
univ-library.ga mail is handled by 10 mx1.hostinger.co.uk.
$ host umd.edu-lib.ml
umd.edu-lib.ml has address 185.28.21.83
umd.edu-lib.ml mail is handled by 0 mx1.hostinger.co.uk.
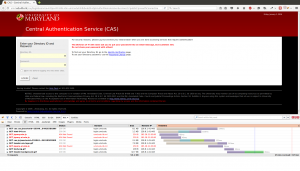
Step 3, The login
The login they created for this account is a pretty convincing copy of UMD’s actual CAS login page. The top/forged one uses graphics from UMD. Looking at the source, the login form has been modified to send the response to save.php.
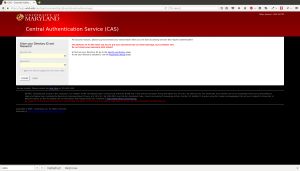
If you go to the root domain, edu-lib.ml, there are a half a dozen other universities listed with what I’m assuming are forged copies of their login pages. Entering any username and password into the password field results in a message saying your services have been activated and a link back to UMD’s library main page.
Overall, I’d have to give this one a B+ for the realness factor. Sadly, it probably picked up quite a few accounts given timing, etc.